Crack the hash Level 1 Write-up (Free Room on TryHackMe) How to Use Hashcat on Linux
Table of contents
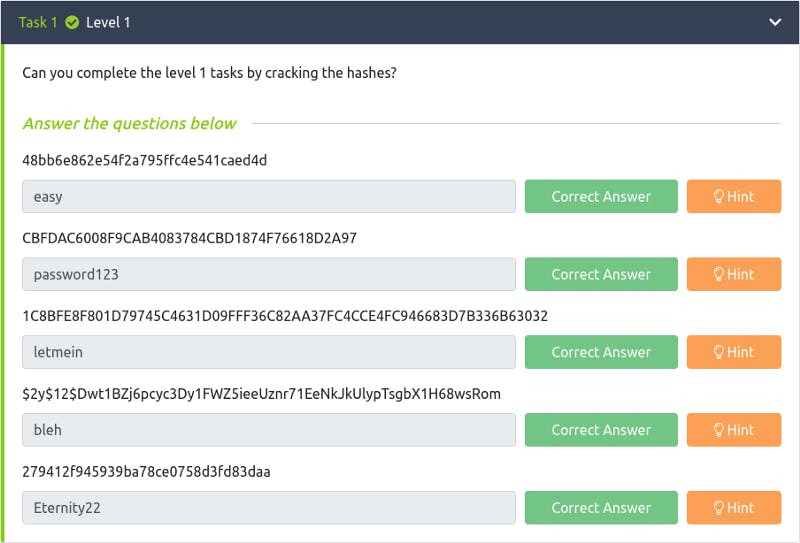
Crack the hash is a free room on TryHackMe, found here. It is rated Easy and contains a series of hashes to be cracked. At first glance I see some hash formats that I instantly recognize, like md5 at level 1 task 1, and others that are much longer or have formats that I haven’t worked with before.
My plan is to start by using CrackStation.net, while also testing against hashcat to demonstrate full understanding. I am using Ubuntu 20.04, so firstly I’m going to install hashcat.
sudo apt install hashcat
And grab the rockyou.txt password list using wget.
wget https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt
Let’s take a look at the tasks…
Pasting the first hash into CrackStation quickly identifies and returns our flag.

We can do the same in hashcat with this command:
hashcat -m 0 48bb6e862e54f2a795ffc4e541caed4d rockyou.txt
Let’s understand this command before we look at the result. Below are excerpts from the manual with option flags of interest as well as the syntax.
dave@ubuntu:~$ man hashcat
NAME
hashcat - Advanced CPU-based password recovery utility
SYNOPSIS
hashcat [options] hashfile [mask|wordfiles|directories]
[....]
OPTIONS
[....]
-m, --hash-type=NUM
Hash-type, see references below
-a, --attack-mode=NUM
Attack-mode, see references below
So in our earlier command we set our hash-type with the -m flag set to 0 or md5.
This table of example hashes from hashcat.net was helpful in quickly identifying which (-m) NUM corresponds to which hash-type, consider bookmarking for later.
We directly pasted our hash into the terminal in our example but from here on out I will save it into a file before running the command on it, I will show this in the next example but after that you will be expected to know that step is included.
The last part of our command is the path to our wordlist which we downloaded with wget earlier.
OKAY, IF YOU ARE STILL WITH ME THAN THANK YOU, LET’S GET TO THE RESULT OF OUR COMMAND:
dave@ubuntu:~$ hashcat -m 0 48bb6e862e54f2a795ffc4e541caed4d rockyou.txt
hashcat (v5.1.0) starting...
[....]
48bb6e862e54f2a795ffc4e541caed4d:easy
Session..........: hashcat
Status...........: Cracked
Hash.Type........: MD5
Hash.Target......: 48bb6e862e54f2a795ffc4e541caed4d
Progress.........: 176128/14344387 (1.23%)
Now we have cracked it with both crackstation and hashcat and gained a basic understanding of how hashcat works.
Time to submit our flag ‘easy’ and move on.

[1–2]
Hash: CBFDAC6008F9CAB4083784CBD1874F76618D2A97
Type: sha1
CrackStation

Quickly put hash into a file:
echo "CBFDAC6008F9CAB4083784CBD1874F76618D2A97" > hash.txt
hashcat command with sha1 hash-type:
hashcat -m 100 hash.txt rockyou.txt
And our output as expected:

We found our flag ‘password123’.

[1–3]
Hash: 1C8BFE8F801D79745C4631D09FFF36C82AA37FC4CCE4FC946683D7B336B63032
Type: sha256
CrackStation

hashcat command:
hashcat -m 1400 hash.txt rockyou.txt
Output:
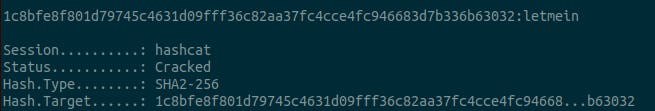
Got the flag, ‘letmein’.
[1–4]
Hash: $2y$12$Dwt1BZj6pcyc3Dy1FWZ5ieeUznr71EeNkJkUlypTsgbX1H68wsRom
Type: BCrypt
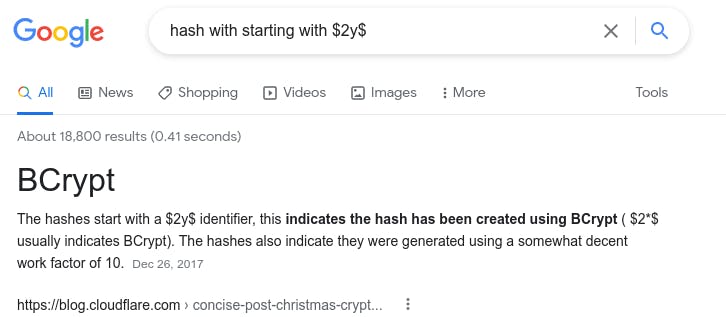
Through a bit of googling I figured out this is a bcrypt hash.
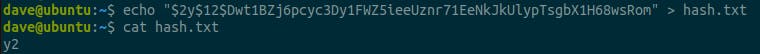
The next issue I ran into was using echo on this hash string which contains $ characters that are special characters in bash. We could add an escape character \$ like so before each but that is 3 extra characters.
From StackOverflow:
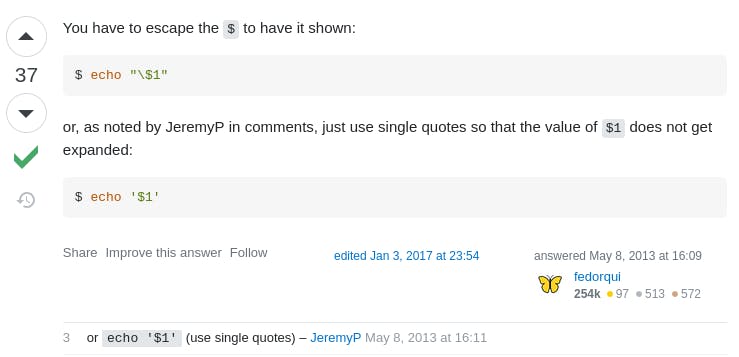
Shoutout to JeremyP in the comments, we can just enclose it in ‘single quotes’ to have the same effect.
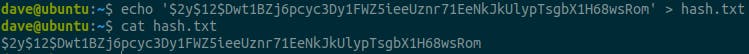
CrackStation

hashcat command:
hashcat -m 3200 hash.txt rockyou.txt
This had an expected completion time of multiple days, but the hint gives good information:
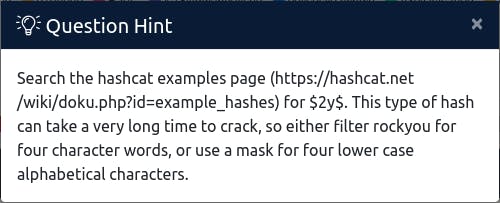
Found this on StackOverflow, to be easily repurposed:
Our command:
awk 'length($0) == 4' rockyou.txt > rockyou_4chars.txt

wc -l command counts the number of lines for us, we chopped it down quite a bit.
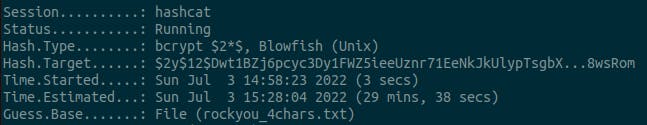
At least this one says it will be finished today.
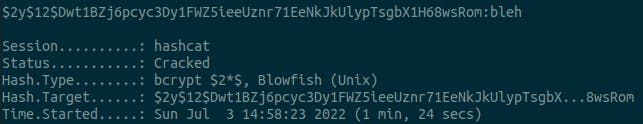
And 1 minute, 24 secs later.. we got the flag, ‘bleh’.
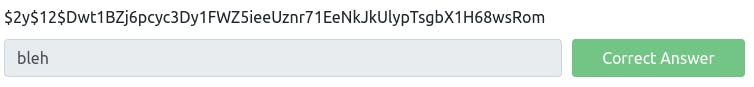
[1–5]
Hash: 279412f945939ba78ce0758d3fd83daa
Type: md4
CrackStation

Trying to copy how we previously used hashcat I made a similar command:
hashcat -m 900 hash.txt rockyou.txt
But this just exhausts the list…


We need to use a custom rule file, dive.rule.
Fetch it with wget:
wget https://github.com/hashcat/hashcat/raw/master/rules/dive.rule
Run our updated hashcat command with -r dive.rule path:
hashcat -a 0 -m 900 hash.txt rockyou.txt -r dive.rule
Got the flag, ‘Eternity22’.
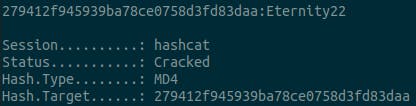
Shoutout to john-the-ripper, took me a lot less time to figure it out there:
john-the-ripper --format=Raw-MD4 hash.txt
Level 1 Conclusion
Success! I hope you got some good information out of this walk-through of TryHackMe’s Crack the hash Level 1. Level 2 coming tomorrow. See you there!
